1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
| #include"Protect.h"
#define SYMBOL L"\\??\\xia0ji2333"
#define WriteCode CTL_CODE (FILE_DEVICE_UNKNOWN,0x803,METHOD_BUFFERED, FILE_ANY_ACCESS)
#define ReadCode CTL_CODE (FILE_DEVICE_UNKNOWN,0x804,METHOD_BUFFERED, FILE_ANY_ACCESS)
#define ReadWriteCode CTL_CODE (FILE_DEVICE_UNKNOWN,0x805,METHOD_BUFFERED, FILE_ANY_ACCESS)
#define ProtectCode CTL_CODE (FILE_DEVICE_UNKNOWN,0x806,METHOD_BUFFERED, FILE_ANY_ACCESS)
#define UnProtectCode CTL_CODE (FILE_DEVICE_UNKNOWN,0x807,METHOD_BUFFERED, FILE_ANY_ACCESS)
NTSTATUS DeviceIrpCtl(PDEVICE_OBJECT driver, PIRP pirp) {
kprintf(("Line %d:xia0ji233: enter IRP Function\n"), __LINE__);
PIO_STACK_LOCATION irpStackL;
ULONG CtlCode;
ULONG InputBuffLength;
irpStackL = IoGetCurrentIrpStackLocation(pirp);
switch (irpStackL->MajorFunction)
{
case IRP_MJ_DEVICE_CONTROL: {
UINT32 code = irpStackL->Parameters.DeviceIoControl.IoControlCode;
kprintf(("Line %d:xia0ji233: ring3 calls DEVICE CONTROL,control code=%x\n"), __LINE__, code);
switch (code) {
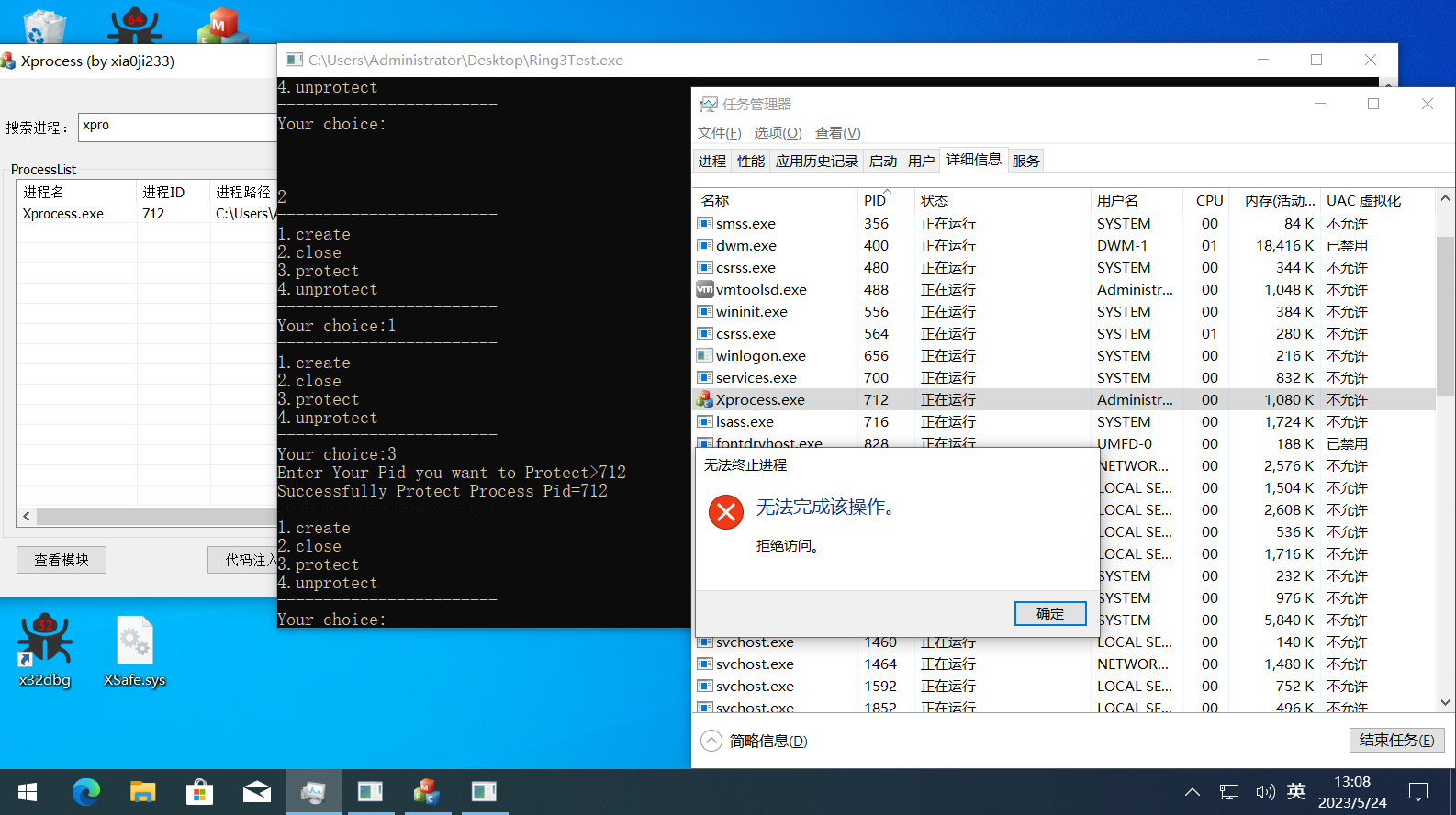
case ProtectCode: {
ULONG PID = *(ULONG *)pirp->AssociatedIrp.SystemBuffer;
kprintf(("Line %d:xia0ji233: start Protect PID=%d\n"), __LINE__,PID);
int i = 0;
while (ProtectPid[i] && i < MAXPROTECT)i++;
pirp->IoStatus.Information = -1;
if (i != MAXPROTECT) {
ProtectPid[i] = PID;
pirp->IoStatus.Information = 0;
}
break;
}
case UnProtectCode: {
ULONG PID = *(ULONG *)pirp->AssociatedIrp.SystemBuffer;
kprintf(("Line %d:xia0ji233: end Protect PID=%d\n"), __LINE__, PID);
int i = 0;
while (ProtectPid[i]!=PID && i < MAXPROTECT)i++;
pirp->IoStatus.Information = -1;
if (i != MAXPROTECT) {
ProtectPid[i] = 0;
pirp->IoStatus.Information = 0;
}
break;
}
}
break;
}
case IRP_MJ_CREATE: {
kprintf(("Line %d:xia0ji233: ring3 calls CREATE\n"), __LINE__);
break;
}
case IRP_MJ_CLOSE: {
kprintf(("Line %d:xia0ji233: ring3 calls CLOSE\n"), __LINE__);
break;
}
default:
break;
}
pirp->IoStatus.Status = STATUS_SUCCESS;
IoCompleteRequest(pirp, IO_NO_INCREMENT);
kprintf(("Line %d:xia0ji233: leave IRP Function\n"), __LINE__);
return STATUS_SUCCESS;
}
NTSTATUS CreateDevice(PDEVICE_OBJECT driver) {
NTSTATUS status;
UNICODE_STRING MyDriver;
PDEVICE_OBJECT device = NULL;
RtlInitUnicodeString(&MyDriver, L"\\DEVICE\\xia0ji233");
status = IoCreateDevice(
driver,
sizeof(driver->DeviceExtension),
&MyDriver,
FILE_DEVICE_UNKNOWN,
FILE_DEVICE_SECURE_OPEN,
FALSE,
&device
);
if (status == STATUS_SUCCESS) {
UNICODE_STRING Sym;
RtlInitUnicodeString(&Sym, SYMBOL);
status = IoCreateSymbolicLink(&Sym, &MyDriver);
if (status == STATUS_SUCCESS) {
kprintf(("Line %d:xia0ji233: symbol linked success\n"), __LINE__);
}
else {
kprintf(("Line %d:xia0ji233: symbol linked failed status=%x\n"), __LINE__, status);
}
}
else {
kprintf(("Line %d:xia0ji233: create device fail status=%x\n"), __LINE__, status);
}
}
void DeleteDevice(PDRIVER_OBJECT pDriver) {
kprintf(("Line %d:xia0ji233: start delete device\n"), __LINE__);
if (pDriver->DeviceObject) {
UNICODE_STRING Sym;
RtlInitUnicodeString(&Sym, SYMBOL);
kprintf(("Line %d:xia0ji233: Delete Symbol\n"), __LINE__);
IoDeleteSymbolicLink(&Sym);
kprintf(("Line %d:xia0ji233: Delete Device\n"), __LINE__);
IoDeleteDevice(pDriver->DeviceObject);
}
kprintf(("Line %d:xia0ji233: end delete device\n"), __LINE__);
}
void DriverUnload(PDRIVER_OBJECT pDriver) {
kprintf(("Line %d:xia0ji233: start unload\n"), __LINE__);
endProtect();
DeleteDevice(pDriver);
}
NTSTATUS DriverEntry(
_In_ PDRIVER_OBJECT DriverObject, _In_ PUNICODE_STRING RegistryPath
) {
typedef struct _LDR_DATA
{
struct _LIST_ENTRY InLoadOrderLinks;
struct _LIST_ENTRY InMemoryOrderLinks;
struct _LIST_ENTRY InInitializationOrderLinks;
VOID* DllBase;
VOID* EntryPoint;
ULONG32 SizeOfImage;
UINT8 _PADDING0_[0x4];
struct _UNICODE_STRING FullDllName;
struct _UNICODE_STRING BaseDllName;
ULONG32 Flags;
}LDR_DATA, *PLDR_DATA;
PLDR_DATA ldr;
ldr = (PLDR_DATA)DriverObject->DriverSection;
ldr->Flags |= 0x20;
startProtect();
DriverObject->DriverUnload = DriverUnload;
DriverObject->MajorFunction[IRP_MJ_CREATE] = DeviceIrpCtl;
DriverObject->MajorFunction[IRP_MJ_CLOSE] = DeviceIrpCtl;
DriverObject->MajorFunction[IRP_MJ_DEVICE_CONTROL] = DeviceIrpCtl;
DriverObject->MajorFunction[IRP_MJ_READ] = DeviceIrpCtl;
DriverObject->MajorFunction[IRP_MJ_WRITE] = DeviceIrpCtl;
CreateDevice(DriverObject);
kprintf(("Line %d:xia0ji233: RegistryPath = %S\n"), __LINE__, RegistryPath->Buffer);
kprintf(("Line %d:xia0ji233: work success\n"), __LINE__);
return 0;
}
|